The First Social Engineering Solution.
You need a real-time, proactive, non-confrontational solution.
Learn How it Works!
Fight Social Engineering with ChallengeWord.
ChallengeWord is the only human driven Social Engineering Solution for malicious cybersecurity attacks. When receiving a suspicious phone call or text message, you need a defense that is easy to use, fast to implement, and highly effective. ChallengeWord is your team's synchronized rotating password that quickly identifies impersonators in a non threatening manner.
The Best Defense is a Good Offense.
Don't wait to be the next target. Take the offense, arm your most valuable assets and greatest vulnerability with ChallengeWord. Put the power of protection in the hands of every member of your team so they no longer fear the unknown. Empower your organization to stop social engineering when and where it happens with ease and confidence.
The Best Defense is a Good Offense.
Don't wait to be the next target. Take the offense, arm your most valuable assets and greatest vulnerability with ChallengeWord. Put the power of protection in the hands of every member of your team so they no longer fear the unknown. Empower your organization with the first social engineering solution.
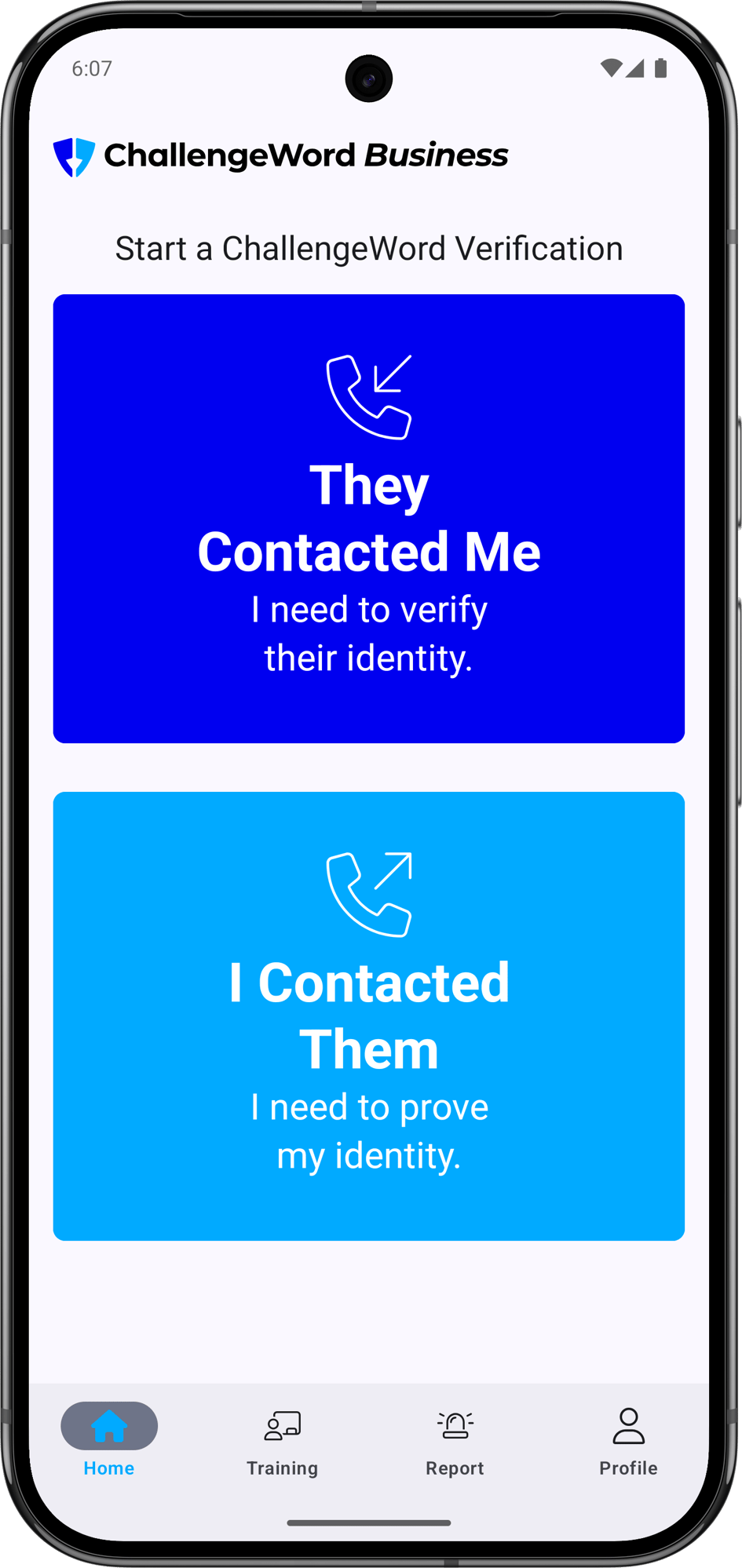
Stop social engineering.
Fast adoption, zero disruption.
Secure more, spend less.
Social Engineering Solution
ChallengeWord offers the ultimate protection against your organization's worst enemy, social engineering hackers. It seamlessly supports your human vulnerabilities: smishing attacks, vishing attacks, social media and in-person attacks. ChallengeWord delivers real-time security against real-life cybersecurity threats.
Don't Take Our Word for it.






ChallengeWord 101
Social Engineering Stats
Your Workplace Vulnerabilities
Join the ChallengeWord Newsletter!
Sign-up for regular updates on the latest cybersecurity trends.
MFA4irl : the Missing Puzzle Piece
Our social engineering solution seamlessly integrates into your existing cybersecurity framework, serving as the missing piece of the puzzle that bolsters your defenses against evolving threats. With its comprehensive features and real-time threat detection, it fortifies your organization's security posture, providing the confidence you need to protect against social engineering attacks effectively.
Turn-Key Solution
Our turn-key solution provides a hassle-free and efficient approach to addressing your specific needs without the complexities of custom integration. From installation to ongoing support, it offers a straightforward way to streamline operations and have everything you need at your fingertips. With rapid implementation, you can start reaping the benefits of our ready-to-use turn-key solution, which is easily adaptable to your organization's unique requirements, ensuring a seamless and hassle-free experience from start to finish.
Web, Mobile, Office
Our solution boasts versatility by being available on all platforms, encompassing web, mobile, and Microsoft Office environments. Whether you're on the go, working at your desk, or collaborating within Office applications, our solution ensures accessibility and consistency across these diverse platforms. This comprehensive coverage not only enhances user convenience but also reinforces the security of your data and operations, ensuring that you have robust protection and functionality regardless of the platform you prefer or the situation you encounter.
SIEM Integration
Our solution offers seamless integration with your Security Information and Event Management (SIEM) system, enhancing your organization's overall security posture. By seamlessly connecting to your SIEM, it enriches the data analysis capabilities and provides real-time threat intelligence, allowing you to detect and respond to security incidents more effectively. This integration streamlines your security operations, providing a unified platform where you can monitor, correlate, and analyze security events comprehensively. As a result, your SIEM becomes a more powerful tool in safeguarding your organization's critical assets, making our solution an invaluable component of your cybersecurity strategy.
Meet Our Awesome Team
Our team has many skills so we’re able to offer a wide array of services. Far away, behind the word mountains, far from the countries Vokalia.

Adam Benwell

Heather Benwell

